Top types of Accounts Payable fraud to watch in 2025
Hear what's covered in this article:
Fraud is evolving as fast as the technology built to stop it, and with accounts payable teams still a top target, staying proactive is essential. Whether it's new AI-driven threats or tried-and-true scams with a modern twist, awareness and proactive action can make all the difference. But there’s no need to be afraid. With the right information and tools, you can protect your business.
In this guide, we’ll explore the top types of accounts payable fraud you need to watch for in 2025 and provide practical strategies for preventing them.
Key Takeaways
Fraud is evolving fast, with AI and new technologies making scams more advanced. Staying alert and proactive is key for accounts payable teams in 2025.
External fraud threats like invoice fraud, phishing, and payment diversion remain major risks. AI tools and strong verification processes are vital.
Internal fraud, including expense and payroll fraud, can be reduced with internal controls, audits, and role-based access.
New fraud threats like AI-driven fraud, deepfakes, and third-party risks require advanced detection tools and awareness.
Fraud prevention strategies include AI tools, team education, multi-factor authentication, and regular audits.
Proactive fraud detection improves security by catching irregularities and strengthening internal controls.
External Accounts Payable Fraud
Invoice Fraud
Invoice fraud may be one attack type you are most familiar with, and that’s good because it’s still a common occurrence and a high priority for AP teams. It occurs when scammers use fake or altered invoices to trick companies into making unauthorized payments. They might pretend to be legitimate vendors or intercept accurate invoices to change the payment details. Some even monitor email conversations to time their attacks just right, copying the tone and style of genuine suppliers.
Red flag: Invoices with unfamiliar or mismatched vendor details, such as changed bank account numbers or minor formatting discrepancies.
Prevention tip: Use AI-powered fraud prevention tools to identify anomalies and flag suspicious invoices before processing payments. Train your AP teams to verify invoices by cross-checking vendor details, purchase orders, and payment history.
Phishing Scams
Phishing attacks became popular as email communication grew in business. It’s now a commonly recognized fraud tactic, but AI is making it harder to differentiate between what’s real and fake. Scammers often pretend to be trusted organizations through emails or messages to steal sensitive information like passwords or financial details. With the rise in AI, scammers are creating emails that look more and more authentic than ever before.
Red flag: Unsolicited emails with a sense of urgency, suspicious links, or attachments, especially those requesting payment or sensitive information.
Prevention tip: Teach your team how to spot phishing scams. Set up strong email security measures like spam filters and domain authentication to keep fake messages out. Adding multi-factor authentication (MFA) gives you an extra layer of security.
Vendor Fraud
Vendor fraud involves fraudsters submitting fake invoices or even hacking legitimate vendor accounts to redirect payments. Common tricks include setting up phony vendor profiles, tweaking real ones, or sending inflated invoices for services that never happened. The good news is you probably know your vendors well, but always take precautions to catch sneaky fraud attempts.
Red flag: Unusual changes to vendor banking details or payment terms, particularly when requested via email or phone without prior confirmation.
Prevention tip: Regularly audit your vendors and use master data management systems to confirm authenticity. AI tools can spot red flags, like sudden changes in payment amounts or timing, that might signal fraud.
Extra security measures
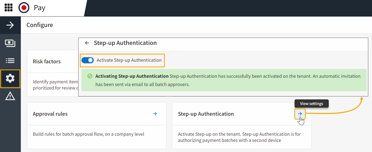
Keep approvers on task with extra security measures.
Adding step-up authentication, like two-factor verification, ensures payments are
made only after invoices and suppliers are thoroughly vetted for fraud and risk.
Payment Diversion Fraud (Business Email Compromise)
You can spot a business email compromise when scammers use fake email addresses or hack into real ones to trick people into sending money to the wrong accounts. Sometimes, they’ll spend months watching internal emails to create requests that seem legitimate. But, don’t worry, there are ways to recognize how to spot them.
Red flag: Watch out for payment rerouting requests with sudden changes in payment instructions or unfamiliar email addresses trying to imitate trusted vendors.
Prevention tip: Verify all payment changes through a second, secure communication channel, such as a phone call to a known contact at the vendor. AI solutions can cross-verify payment data and flag discrepancies in payment requests.

-
44% of businesses have been targeted by invoice fraud
-
Business Email Compromise (BEC) scams hit 43% of businesses surveyed
Internal Accounts Payable Fraud
Expense Reimbursement Fraud
Internal fraud can be even more alarming and unsettling, but it does happen, and it’s growing fast. Expense reimbursement fraud is one of the more common internal fraud types. This happens when employees submit fake claims, like inflated travel costs, duplicate receipts, or made-up purchases for reimbursement. For example, someone might try to pass off personal expenses as business ones.
Red flag: Duplicate or excessively high reimbursement requests, receipts for unusual amounts, or expenses submitted shortly after company events or trips.
Prevention tip: Implement automated expense management systems with AI to verify receipts and flag irregularities. Cross-check expenses against travel itineraries or company policies and conduct regular audits to uncover patterns of abuse.
Payroll Fraud
That paycheck seem out of whack? It’s likely payroll fraud. Payroll fraud can include fake employees, padded hours, or unauthorized raises sneaking into the payroll system. For example, a payroll manager might set up a fake employee to funnel money or tweak timekeeping records to show extra hours.
Red flag: Unexplained overtime increases or ghost employees receiving payments without corresponding work records.
Prevention tip: Regular audits and splitting up responsibilities can help reduce risk. Role-based access controls ensure that no one person has full control over payroll tasks. AI tools can also review payroll data to spot things like payments to unregistered accounts or unusual pay increases.
Internal Financial Fraud
Internal financial fraud can happen when employees misappropriate company funds, manipulate financial records, or issue unauthorized payments. Kickback schemes with vendors, where employees receive incentives in exchange for approving fraudulent invoices, are also typical.
Red flag: Employees showing unusually close relationships with vendors, consistently approving high-value invoices, or splitting payments to avoid triggering approval limits.
Prevention tip: Put stronger internal controls in place, like requiring dual approvals for big transactions. Create a whistleblower-friendly environment by setting up anonymous reporting channels. Fraud detection tools can also help by flagging split transactions or unusually large amounts.
Data Manipulation Fraud
Don’t let little details cause big losses. Data manipulation can be easy to do in the wrong hands. Employees might change data to hide theft or make the company’s finances look better than they really are. For instance, they could tweak inventory records to cover up stolen items or adjust financial statements to hit performance goals.
Red flag: Inconsistent or rapidly changing financial data, such as discrepancies between inventory records and financial reports.
Prevention tip: Use advanced analytics tools to monitor data integrity and spot any anomalies. Schedule regular, independent audits of financial records and processes. Set up role-based access for sensitive data to reduce the chances of manipulation.

Ready to protect your business
from AP fraud in 2025?
Learn more about Medius Fraud & Risk Detection.
Increasing Threats in 2025
ACH Fraud
ACH fraud is still a common threat to look for this year. It happens when scammers get into a company’s Automated Clearing House (ACH) network and redirect payments into their own accounts. These transactions can go unnoticed, making it a serious issue for accounts payable teams.
Red flag: Unusual ACH payment routing details changes, especially from new or unverified sources.
Prevention tip: Implement robust ACH fraud detection systems that monitor irregular transactions and require dual authentication for changes to payment details.
AI-powered Fraud
AI, AI, AI…it’s everywhere, and AI makes creating convincing phishing emails and fake vendor messages and bypass detection systems easier. These tools adapt and learn from security defenses, making their attacks smarter and more challenging to catch over time.
Red flag: Phishing emails or communications that seem increasingly personalized or persuasive, with a tone and style that mimic familiar communications.
Prevention tip: Incorporate AI-driven fraud detection tools, like Medius Fraud & Risk Detection, that stay ahead of evolving fraud tactics and protect against AI-powered scams.
Deepfake Technology
Deepfake fraud is rising, and technology is making it easier than ever. In fact, 53% of finance professionals report being targeted by deepfake scams. These voice and video deepfakes can imitate executives so convincingly that they trick AP teams into approving fake payments. By mimicking the voice or appearance of senior leaders, scammers are making it harder to identify fraud and easier to slip through the cracks.
Red flag: Payment requests that seem out of the ordinary with suspicious tones or urgent requests, especially if they involve executive-level authority.
Prevention tip: Train employees to question unusual payment requests, even if they appear to come from top management. Implement strong internal verification procedures like face-to-face confirmation or encrypted communication channels.
Third-party Risks
Stay protected from third party risks. Increased reliance on vendors and outsourced AP processes expands the attack surface for fraudsters. As AP systems become more interconnected, the risk of fraud through third-party relationships increases.
Red flag: Unverified or new vendors making urgent payment requests or frequent changes to vendor details from external partners.
Prevention tip: Regularly assess third-party security and vendor management processes. Use automated systems to monitor third-party transactions for signs of fraud or errors.
Be proactive and prepared
with Medius
Fraud in 2025 will be more dynamic than ever, but staying proactive with robust tools
like Medius Fraud & Risk Detection can ensure your AP processes remain secure.
Be vigilant, use technology to your advantage, and don’t wait for fraud to strike—
act now to protect your business.